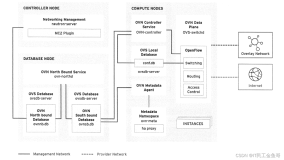
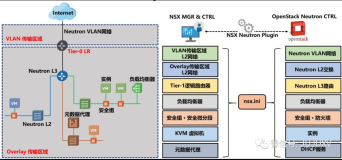
参考官方资料
You must modify the rules for the default security group because users cannot access instances that use the default group from any IP address outside the cloud. You can modify the rules in a security group to allow access to instances through different ports and protocols. For example, you can modify rules to allow access to instances through SSH, to ping them, or to allow UDP traffic – for example, for a DNS server running on an instance. You specify the following parameters for rules: Source of traffic. Enable traffic to instances from either IP addresses inside the cloud from other group members or from all IP addresses. Protocol. Choose TCP for SSH, ICMP for pings, or UDP. Destination port on virtual machine. Defines a port range. To open a single port only, enter the same value twice. ICMP does not support ports: Enter values to define the codes and types of ICMP traffic to be allowed. Rules are automatically enforced as soon as you create or modify them.
注: 已通过测试, 修改默认 secgroup 或自定义 secgroup 都可以完成数据访问测试
帮助
[root@station140 ~(keystone_admin)]# nova help | grep secgroup
add-secgroup Add a Security Group to a server.
list-secgroup List Security Group(s) of a server.
remove-secgroup Remove a Security Group from a server.
secgroup-add-group-rule
secgroup-add-rule Add a rule to a security group.
secgroup-create Create a security group.
secgroup-delete Delete a security group.
secgroup-delete-group-rule
secgroup-delete-rule
secgroup-list List security groups for the current tenant.
secgroup-list-rules
secgroup-update Update a security group.
创建自定义安全组
[root@station140 ~(keystone_admin)]# nova secgroup-create terry "allow ping and ssh" +--------------------------------------+-------+--------------------+ | Id | Name | Description | +--------------------------------------+-------+--------------------+ | 6966a8e4-0980-40ad-a409-baac65b60287 | terry | allow ping and ssh | +--------------------------------------+-------+--------------------+
列出当前所有安全组
[root@station140 ~(keystone_admin)]# nova secgroup-list +--------------------------------------+---------+--------------------+ | Id | Name | Description | +--------------------------------------+---------+--------------------+ | 91a191a6-b89e-4f87-99c0-0fb985985978 | default | default | | 6966a8e4-0980-40ad-a409-baac65b60287 | terry | allow ping and ssh | +--------------------------------------+---------+--------------------+
列出某个组中的安全规则
[root@station140 ~(keystone_admin)]# nova secgroup-list-rules default +-------------+-----------+---------+----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+----------+--------------+ | | | | | default | | | | | | default | +-------------+-----------+---------+----------+--------------+
增加规则方法 (允许 ping)
[root@station140 ~(keystone_admin)]# nova secgroup-add-rule terry icmp -1 -1 0.0.0.0/0 +-------------+-----------+---------+-----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+-----------+--------------+ | icmp | -1 | -1 | 0.0.0.0/0 | | +-------------+-----------+---------+-----------+--------------+
增加规则方法 (允许 ssh)
[root@station140 ~(keystone_admin)]# nova secgroup-add-rule terry tcp 22 22 0.0.0.0/0 +-------------+-----------+---------+-----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+-----------+--------------+ | tcp | 22 | 22 | 0.0.0.0/0 | | +-------------+-----------+---------+-----------+--------------+
增加规则方法 (允许 dns 外部访问)
[root@station140 ~(keystone_admin)]# nova secgroup-add-rule terry udp 53 53 0.0.0.0/0 +-------------+-----------+---------+-----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+-----------+--------------+ | udp | 53 | 53 | 0.0.0.0/0 | | +-------------+-----------+---------+-----------+--------------+
列出自定义组规则
[root@station140 ~(keystone_admin)]# nova secgroup-list-rules terry +-------------+-----------+---------+-----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+-----------+--------------+ | tcp | 22 | 22 | 0.0.0.0/0 | | | udp | 53 | 53 | 0.0.0.0/0 | | | icmp | -1 | -1 | 0.0.0.0/0 | | +-------------+-----------+---------+-----------+--------------+
尝试修改 default secgroup
列出 default secgroup 规则
[root@station140 ~(keystone_admin)]# nova secgroup-list-rules default +-------------+-----------+---------+----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+----------+--------------+ | | | | | default | | | | | | default | +-------------+-----------+---------+----------+--------------+
添加规则 (允许 ping)
[root@station140 ~(keystone_admin)]# nova secgroup-add-rule default icmp -1 -1 0.0.0.0/0 +-------------+-----------+---------+-----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+-----------+--------------+ | icmp | -1 | -1 | 0.0.0.0/0 | | +-------------+-----------+---------+-----------+--------------+
添加规则 (允许 ssh)
[root@station140 ~(keystone_admin)]# nova secgroup-add-rule default tcp 22 22 0.0.0.0/0 +-------------+-----------+---------+-----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+-----------+--------------+ | tcp | 22 | 22 | 0.0.0.0/0 | | +-------------+-----------+---------+-----------+--------------+
添加规则 (允许 dns外部访问)
[root@station140 ~(keystone_admin)]# nova secgroup-add-rule default udp 53 53 0.0.0.0/0 +-------------+-----------+---------+-----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+-----------+--------------+ | udp | 53 | 53 | 0.0.0.0/0 | | +-------------+-----------+---------+-----------+--------------+
列出默认组规则
[root@station140 ~(keystone_admin)]# nova secgroup-list-rules default +-------------+-----------+---------+-----------+--------------+ | IP Protocol | From Port | To Port | IP Range | Source Group | +-------------+-----------+---------+-----------+--------------+ | | | | | default | | icmp | -1 | -1 | 0.0.0.0/0 | | | tcp | 22 | 22 | 0.0.0.0/0 | | | | | | | default | | udp | 53 | 53 | 0.0.0.0/0 | | +-------------+-----------+---------+-----------+--------------+
删除某个实例, 使用中的规则
nova remove-secgroup terry_instance1 terry
注: 在虚拟机启动后, 无法在增加其他规则