Well, you can be quite frustrated when beloved FGdump just does not work without particular reason. Password hashes are so close, but yet not achievable. But it seems there is a kind of remedy (or call it: “alternative way”) for getting the password hashes. Here is the story.
All right, we know that password hashes are stored in the registry, in the key HKLM/Security/Sam. Normally you must have administrator privileges to access it. Even you are the local admin – you still have to assign manually full control permission for this subkey to yourself. Then you may see something like this:
The juicy stuff physically is stored in two files:
C:/windows/system32/config/sam
and
C:/windows/system32/config/system
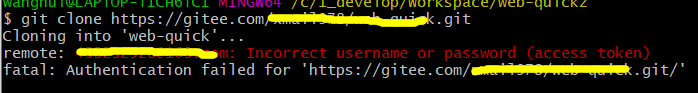
So theoretically if we would be able to get the content of those files we may pass it to Cain and play a little with it… But unfortunately those files are locked, so they can’t be copied or accesses by any way. If you will try, you will immediately have a nice error like this:
So it looks like no chance. Well, note quite. There is an interesting approach called “Dumping File Sectors Directly from Disk using Logical Offsets”, which surprisingly allow you to copy files which are locked and currently used. There is nice tool called FDump which allows you to do this. More details here: http://www.codeproject.com/KB/files/FDump.aspx
If you don’t want to go to deep into the theory (which is recommended btw), - here is the practical solution.
The target:
We must have own separate copies of both files: C:/windows/system32/config/sam and C:/windows/system32/config/system in target system (the second one is needed because of the “boot key” is stored there) so then we may process it somewhere else with Cain & Abel.
Step 1:
Run the fdump.exe with the following parameters:
fdump.exe "C:/WINDOWS/system32/config/SAM" sam.dat fdump.exe "C:/WINDOWS/system32/config/system" system.dat
Expected result:
Step 2:
Run cain.exe and do the following thing: Select “Cracker”, then “Add to list” and then “Import hashes from Sam database”.
Then:
So after all manipulations it should looks more or less like this:
Then click “Next”, and here we are!
The rest is up to you. Now you probably need a good rainbow tables and a bit of luck. :-)
Afterword:
You may be tempted to explore the copied registry manually and see what else is there (your curiosity is more then normal), so here is the quick "how to" browse downloaded registry files with regedit:
Open regedit, and make single click on HKLM branch (important!):
Then in the main menu select “File” and “Load Hive”, then select our file: C:/myfiles/sam
...and finally provide a key name. This is the key where a new hive will be attached to.
Do not forget to assign proper permissions to this branch:
Close the regedit and open it again. Now you can browse everything! :)